The Atomic Stealer malware attacks macOS through counterfeit browser updates.
The 'ClearFake' fake browser update campaign is now targeting Apple computers with Atomic Stealer (AMOS) malware, extending its reach to macOS. [...]

The 'ClearFake' campaign, initially targeting Windows users with counterfeit Chrome update prompts, has expanded its reach to macOS, now deploying the Atomic Stealer (AMOS) malware to Apple computers.
Launched in July, ClearFake leveraged JavaScript injections on compromised websites to trick users into downloading malicious updates. By October 2023, Guardio Labs uncovered a novel aspect of the campaign: the use of Binance Smart Chain contracts to conceal its harmful scripts within the blockchain, a method termed "EtherHiding." This strategy facilitated the distribution of malware designed for Windows, including data thieves like RedLine, Amadey, and Lumma.
The latest shift in ClearFake's strategy, as reported by threat analyst Ankit Anubhav on November 17, 2023, marks a significant turn. The campaign has begun distributing DMG payloads to macOS users who visit these infected sites. A recent Malwarebytes report corroborates this change, noting that these macOS-targeted attacks use not only the familiar Chrome update guise but also fake Safari update prompts.
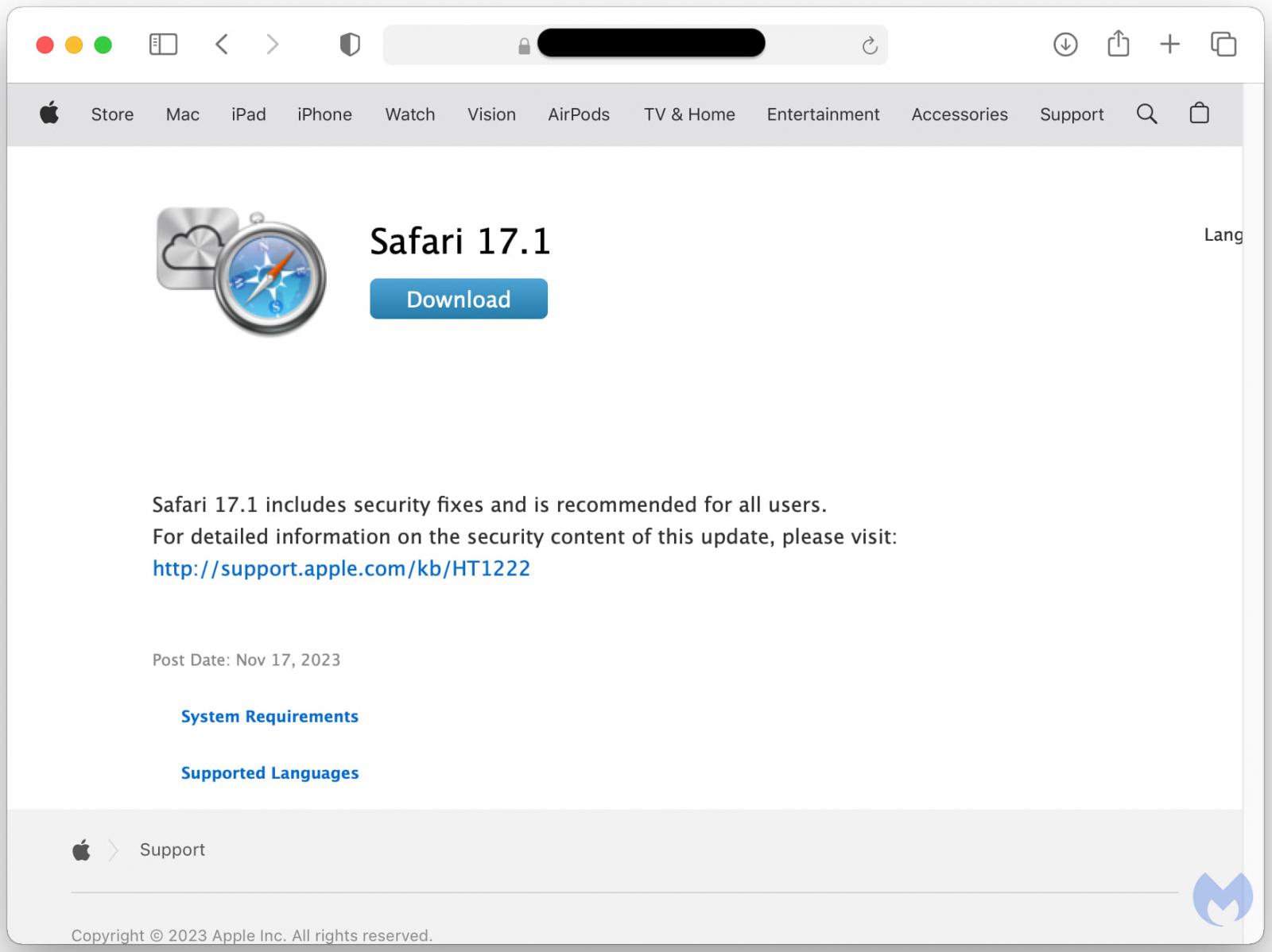
Source: Malwarebytes
The payload dropped in these cases is Atomic, an info-stealing malware sold to cybercriminals via Telegram channels for $1,000/month.
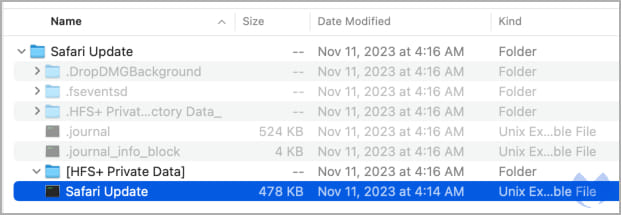
Source: Malwarebytes
Atomic, a malware first identified in April 2023 by Trellix and Cyble, is known for its ability to extract sensitive information. It targets a range of data including passwords, cookies, and credit card details stored in browsers, local files, and over 50 cryptocurrency extensions. One of its key targets is the macOS keychain password manager, which stores a variety of encrypted information such as WiFi passwords, website logins, and credit card data. A breach of this system could lead to significant consequences for the victim.
An analysis conducted by Malwarebytes on the malware's payload revealed various commands designed to extract critical data. These include commands to access passwords and document files, images, cryptocurrency wallet files, and keys, underlining the broad spectrum of sensitive data at risk from Atomic attacks.
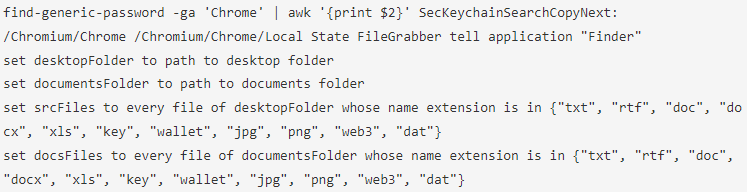
Source: Malwarebytes
The expansion of the ClearFake campaign to target Mac users serves as an important alert for those in the Apple ecosystem to enhance their cybersecurity vigilance, particularly when downloading software. Despite awareness about the Atomic malware for several months, about half of antivirus engines on VirusTotal still fail to detect this payload.
It's crucial to remember that legitimate Safari browser updates are always distributed via macOS's Software Update feature. For other browsers, updates are typically available directly within the browser itself. Consequently, any website pop-ups or prompts suggesting browser updates should be treated with skepticism and generally disregarded to avoid potential security risks.























![Largest Data Breaches in US History [Updated for 2023]](https://nulld3v.com/uploads/images/202311/image_430x256_654e69df8d469.jpg)










![[code] WordPress Plugin AN_Gradebook <= 5.0.1 - Subscriber+ SQLi](https://nulld3v.com/uploads/images/202311/image_430x256_654d29af21505.jpg)


