The Top 72 Most Significant Data Breaches in History
Our revised 2023 list ranks the top 72 most impactful data breaches of all time. Learn from these incidents to prevent expensive damages.
The rising trend in data breaches continues to angle upwards, and as a result, there has never been a more precarious time in history to launch and maintain a successful business.
To prevent the repetition of mistakes that result in data theft, we’ve compiled a list of the 72 biggest data breaches in history, which includes the most recent data breaches in February 2022.
As you’ll see, even prestigious companies like Facebook, LinkedIn, and Twitter are vulnerable to the rising trend of data breaches.
You may also be interested in our list of biggest data breaches in the finance and healthcare industries.
The 72 Biggest Data Breaches Ranked by Impact
Each of the data breaches reveals the mistakes that lead to the exposure of up to millions of personal data records .
1. CAM4 Data Breach

Date: March 2020
Impact: 10.88 billion records.
Adult video streaming website CAM4 has had its Elasticsearch server breached exposing over 10 billion records.
The breached records included the following sensitive information:
- Full names
- Email addresses
- Sexual orientation
- Chat transcripts
- Email correspondence transcripts
- Password hashes
- IP addresses
- Payment logs
Many of the exposed email addresses are linked to cloud storage services. If hackers were to launch successful phishing attacks on these users, they could gain deeper access to personal photos and business information.
Due to the licentious connection of the breached database, compromised users could fall victim to blackmail and defamation attempts for many years to come.
2. Yahoo Data Breach (2017)

Date: October 2017
Impact: 3 billion accounts
Yahoo disclosed that a breach in August 2013 by a group of hackers had compromised 1 billion accounts. In this instance, security questions and answers were also compromised, increasing the risk of identity theft. The breach was first reported by Yahoo while in negotiations to sell itself to Verizon, on December 14, 2016. Yahoo forced all affected users to change passwords and to reenter any unencrypted security questions and answers to re-encrypt them.
However, by October of 2017, Yahoo changed the estimate to 3 billion user accounts. An investigation revealed that users' passwords in clear text, payment card data and bank information were not stolen. Nonetheless, this remains one of the largest data breaches of this type in history.
3. Aadhaar Data Breach

Date: March 2018
Impact: 1.1 billion people
In March of 2018, it became public that the personal details of more than a billion citizens in India stored in the world’s largest biometric database could be bought online.
This massive data breach was the result of a data leak on a system run by a state-owned utility company. The breach allowed access to the private information of Aadhaar holders, exposing their names, their unique 12-digit identity numbers, and their bank details.
The type of information exposed included the photographs, thumbprints, retina scans and other identifying details of nearly every Indian citizen.
4. Alibaba Data Breach

Date: July 2022
Impact: 1.1 billion users
In mid-2022, Chinese e-commerce giant Alibaba suffered a major data breach that contained customer data including:
- Names
- ID numbers
- Phone numbers
- Physical addresses
- Criminal records
- Online papers
In total, over 23 terabytes of data had been compromised from Alilbaba's cloud hosting servers, Alibaba Cloud, also the largest public cloud service provider in China. The breach was first announced by a hacker through online forums, claiming to have data on the Shanghai police force, whose data was also hosted on Alibaba Cloud. Alibaba and its founder, Jack Ma, faced massive criticism for leaving critical servers completely unprotected with no password lock, despite handling extremely sensitive government information.
This was not Alibaba's first data breach incident, as just one year earlier, they were exposed by a third-party developer who had been scraping Alibaba's shopping site, TaoBao, for user data. Again, over a billion users were exposed and despite a three-year prison sentence for the developer and his employer, Alibaba showed that they continued to practice lax security going into 2022.
5. First American Financial Corporation Data Breach

Date: May 2019
Impact: 885 million users
In May 2019, First American Financial Corporation reportedly leaked 885 million users' sensitive records that date back more than 16 years, including bank account records, social security numbers, wire transactions, and other mortgage paperwork. The leak occurred through a website configuration error, allowing the public to view sensitive information without needing any authentication. Because First American's records were sequential, anyone could increase or decrease the number in the URL to quickly view another customer's records. Despite the massive leak, there were no reports of any customer information being stolen and used for malicious purposes.
6. Verifications.io Data Breach

Date: February 2019
Impact: 763 million users
In February 2019, email address validation service verifications.io exposed 763 million unique email addresses in a MongoDB instance that was left publicly facing with no password. Many records also included names, phone numbers, IP addresses, dates of birth and genders.
7. LinkedIn Data Breach (2021)

Date: June 2021
Impact: 700 million users
Data associated with 700 million LinkedIn users was posted for sale in a Dark Web forum on June 2021. This exposure impacted 92% of the total LinkedIn user base of 756 million users.
The data was dumped in two waves, initially exposing 500 million users, and then a second dump where the hacker "God User" boasted that they were selling a database of 700 million LinkedIn.
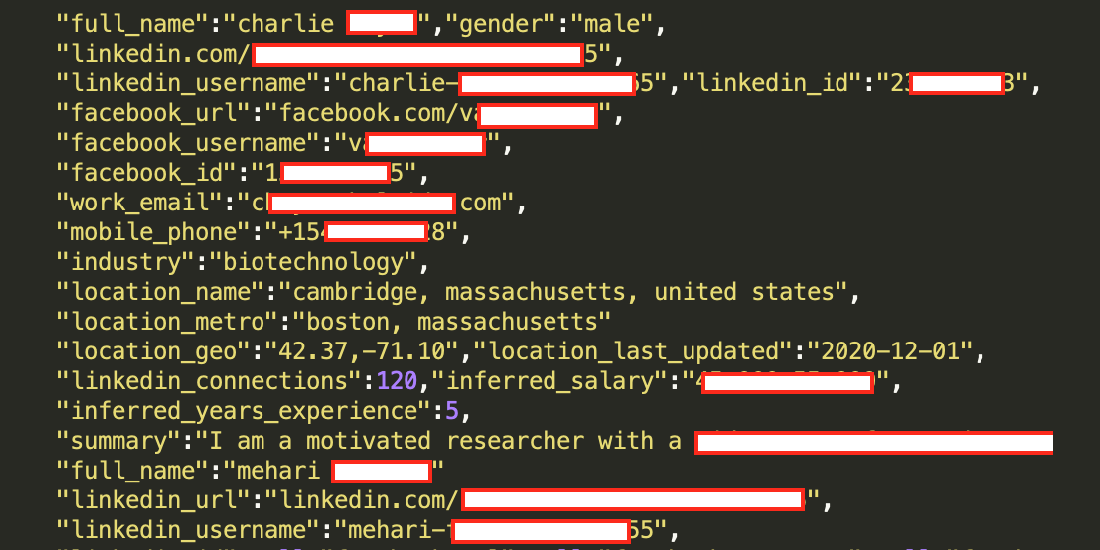
The hackers published a sample containing 1 million records to confirm the legitimacy of the breach. The data included the following:
- Email addresses
- Full names
- Phone numbers
- Geolocation records
- LinkedIn username and profile URLs
- Personal and professional experience
- Genders
- Other social media accounts and details
The hacker scraped the data by exploiting LinkedIn's API.
LinkedIn claims that, because personal information was not compromised, this event was not a 'data breach but, rather, just a violation of their terms of service through prohibited data scraping.
But the leaked data is sufficient to launch a deluge of cyberattacks targeting exposed users, which makes the incident heavily weighted towards a data breach classification.
8. Facebook Data Breach (2019)

Date: April 2019
Impact: 533 million users
In April 2019, the UpGuard Cyber Risk team revealed two third-party Facebook app datasets had been exposed to the public Internet. One, originating from the Mexico-based media company Cultura Colectiva, weighs in at 146 gigabytes and contains over 533 million records detailing comments, likes, reactions, account names, FB IDs and more. This same type of collection, in similarly concentrated form, has been cause for concern in the recent past, given the potential uses of such data. Read more about this Facebook data breach here.
This database was leaked on the dark web for free in April 2021, adding a new wave of criminal exposure to the data originally exfiltrated in 2019. This makes Facebook one of the recently hacked companies 2021, and therefore, one of the largest companies to be hacked in 2021.
— Alon Gal (Under the Breach) (@UnderTheBreach) April 3, 2021All 533,000,000 Facebook records were just leaked for free.
This means that if you have a Facebook account, it is extremely likely the phone number used for the account was leaked.
I have yet to see Facebook acknowledging this absolute negligence of your data. https://t.co/ysGCPZm5U3 pic.twitter.com/nM0Fu4GDY8
9. Yahoo Data Breach (2014)

Date: 2014
Impact: 500 million accounts
Yahoo believed that a "state-sponsored actor" was behind this initial cyberattack in 2014. The stolen data included personal information such as names, email addresses, phone numbers, hashed passwords, birth dates, and security questions and answers, some of which were unencrypted. Yahoo had become aware of this breach back in 2014, taking a few initial remedial actions but failing to investigate further. It was only about two years later that Yahoo publicly disclosed the breach after a stolen database from the company allegedly went up for sale on the black market.
10. Starwood (Marriott) Data Breach

Date: November 2018
Impact: 500 million guests
In November 2018, Marriott International announced that hackers had stolen data about approximately 500 million Starwood hotel customers. The attackers had gained unauthorized access to the Starwood system back in 2014 and remained in the system after Marriott acquired Starwood in 2016. However, the discovery was not made until 2018.
The information that was exposed included names, contact information, passport number, Starwood Preferred Guest numbers, travel information, and other personal information. Marriott believes that financial information such as credit and debit card numbers, and expiration dates of more than 100 million customers were stolen, although the company is uncertain whether the attackers were able to decrypt the credit card numbers.
According to the New York Times, the breach was eventually attributed to a Chinese intelligence group, The Ministry of State Security, seeking to gather data on US citizens. If true, this would be the largest known breach of personal data conducted by a nation-state.
11. Adult Friend Finder Data Breach

Date: October 2016
Impact: 412.2 million accounts
In October 2016, hackers collected 20 years of data on six databases that included names, email addresses and passwords for The AdultFriendFinder Network. The FriendFinder Network includes websites like Adult Friend Finder, Penthouse.com, Cams.com, iCams.com, and Stripshow.com.
Most of the passwords were protected only by the weak SHA-1 hashing algorithm, which meant that 99% of them had been cracked by the time LeakedSource.com published its analysis of the entire data set on November 14.
12. MySpace Data Breach

Date: June 2013
Impact: 360 million accounts
In June 2013 around 360 million MySpace accounts were compromised by a Russian hacker, but the incident was not publicly disclosed until 2016. The information that was leaked included account information such as the owner’s listed name, username, and birthdate. Between 2013 and 2016, anyone who gained access to this breached information could have taken over any Myspace account. The former social media network giant has since invalidated all passwords belonging to accounts that were set up prior to 2013.
13. Exactis Data Breach

Date: June 2018
Impact: 340 million people
In June of 2018, Florida-based marketing and data aggregation firm Exactis exposed a database containing nearly 340 million records on a publicly accessible server. The breach exposed highly personal information such as people's phone numbers, home, and email addresses, interests, and the number, age, and gender of their children. This data exposure was discovered by security expert Vinny Troia, who indicated that the breach included data on hundreds of millions of US adults and millions of businesses.
14. Twitter Data Breach (2018)

Date: May 2018
Impact: 330 million users
In May of 2018, social media giant Twitter notified users of a glitch that stored passwords unmasked in an internal log, making all user passwords accessible to the internal network. Twitter told its 330 million users to change their passwords but the company said it fixed the bug and that there was no indication of a breach or misuse, but encouraged the password update as a precaution. Twitter did not disclose how many users were impacted but indicated that the number of users was significant and that they were exposed for several months.
15. NetEase Data Breach

Date: October 2015
Impact: 234 million users
In October 2015, NetEase (located at 163.com) was reported to suffered from a data breach that impacted hundreds of millions of subscribers. While there is evidence to say that the data is legitimate (many users confirmed their passwords where in the data), it is difficult to verify emphatically.
The breach contained email addresses and plain text passwords.
16. Sociallarks Data Breach

Date: January 2021
Impact: 200 million records
Sociallarks, a rapidly growing Chinese social media agency suffered a monumental data leak in 2021 through its unsecured ElasticSearch database.
Sociallarks’ server wasn’t password-protected, wasn’t encrypted, and it was a publicly exposed asset. This lethal combination meant that anybody with knowledge of the server IP address could access the leaked sensitive data, and that’s exactly what happened.
The breached database stored the scraped data of over 200 million Facebook, Instagram, and Linkedin users.
Exposed data included:
- Names
- Phone numbers
- Email addresses
- Profile descriptions
- Follower and engagement data
- Locations
- LinkedIn profile links
- Connected social media account login names
17. Deep Root Analytics Data Breach

Date: Jun 2017
Impact: 200 million U.S voters
The records of 200 million voters was accessed from Deep Root Analytics, a firm working on behalf of the Republican National Committee (RNC).
The data consisted of 1.1 terabytes of voter Personal Identifiable Information (PII) including names, addresses and birthdates.
The accessed data also contained comprehensive voter analysis based on Reddit post activity which could be used to predict how somebody would vote on a particular issue.
The breached database was discovered by the UpGuard Cyber Research team.
18. Court Ventures Data Breach

Date: Oct 2013
Impact: 200 million personal records
Court Ventures, a subsidiary of credit card monitoring firm Experian, was breached exposing 200 million personal records.
The hacker was running a business selling Personal Identifiable Information and was selling the credit card numbers and social security numbers he had accessed in the breach.
Penetration was achieved by the hacker posing as a private investigator from Singapore and convincing staff to relinquish access to the internal database.
Experian suffered another breach in 2020, when a threat actor claiming to be Experian's client convinced staff to relinquish customer information for marketing purposes.
These events have earned Experian the reputation of suffering one the biggest data breaches in the financial services sector.
19. LinkedIn Data Breach

Date: June 2012
Impact: 165 million users
In June 2012, LinkedIn disclosed a data breach had occurred, but password-reset notifications at the time indicated that only 6.5 million user accounts had been affected. LinkedIn never confirmed the actual number, and in 2016, we learned why: a whopping 165 million user accounts had been compromised, including 117 million passwords that had been hashed but not "salted" with random data to make them harder to reverse.
That revelation prompted other services to comb their LinkedIn data and force their own users to change any passwords that matched (kudos to Netflix for taking the lead on this one.) Left unanswered is why LinkedIn did not further investigate the original breach, or inform more than 100 million affected users, in the intervening four years.
20. Dubsmash Data Breach

Date: December 2018
Impact: 162 million users
In December 2018, Dubmash suffered a data breach that exposed 162 million unique email addresses, usernames and DBKDF2 password hashes. In 2019, this data appeared for sale on a dark web marketplace, where stolen data is usually sold with Bitcoin currency.
21. Adobe Data Breach

Date: October 2013
Impact: 152 million
In October 2013, 153 million Adobe accounts were breached. The data breach contained an internal ID, username, email, encrypted password and password hint in plain text. The encryption was weak and many were quickly resolved back to plain text, the password hints added to the damage making it easy to guess the passwords of many users.
22. MyFitnessPal Data Breach

Date: February 2018
Impact: 150 million users
In February 2018, the diet and exercise app MyFitnessPal (owned by Under Armour) suffered a data breach, exposing 144 million unique email addresses, IP addresses and login credentials such as usernames and passwords stored as SHA-1 and bcrypt hashes (the former for earlier accounts, the latter for newer accounts). In 2019, this sensitive data appeared listed for sale on a dark web marketplace and began circulating more broadly, so it was identified and provided to data security website Have I Been Pwned.
23. Equifax Data Breach

Date: September 2017
Impact: 148 million people
In September 2017, Equifax, one of the three largest consumer credit reporting agencies in the United States, announced that its systems had been breached and the sensitive personal data of 148 million Americans had been compromised. The data compromised included names, home addresses, phone numbers, dates of birth, social security numbers, and driver’s license numbers. The credit card information of approximately 209,000 consumers was also exposed through this data breach. The sensitivity of the information processed by Equifax makes this breach unprecedented, and one of the largest data breaches to date.
24. eBay Data Breach

Date: February/March 2014
Impact: 145 million users
Between February and March 2014, eBay was the victim of a breach of encrypted passwords, which resulted in asking all of its 145 million users to reset their password. Attackers used a small set of employee credentials to access this trove of user data. The stolen information included encrypted passwords and other personal information, including names, e-mail addresses, physical addresses, phone numbers and dates of birth. The breach was disclosed in May 2014, after a month-long investigation by eBay.
25. Canva Data Breach

Date: May 2019
Impact: 137 million users
In May 2019, Australian business, Canva - an online graphic design tool - suffered a data breach that impacted 137 million users. The exposed data included email addresses, names, usernames, cities and passwords stored as bcrypt hashes.
The suspected culprit(s) — Gnosticplayers — contacted ZDNet to boast about the incident, saying that Canva had detected and remediate the cyber threat that caused the data breach. The attacker also claimed to have gained OAuth login tokens for users who signed in via Google.
Canva confirmed the incident, notified users, and prompted them to change passwords and reset OAuth tokens. This event was one of the biggest data breaches in Australia.
26. Heartland Payment Systems Data Breach

Date: March 2008
Impact: 134 million credit cards exposed
At the time of the breach, Heartland was processing north of 100 million credit card transactions per month for 175,000 merchants. The breach was discovered by Visa and MasterCard in January 2009 when Visa and MasterCard notified Heartland of suspicious transactions. The attackers exploited a known vulnerability to perform a SQL injection attack.
The company paid an estimated $145 million in compensation for fraudulent payments.
27. Apollo Data Breach

Date: July 2018
Impact: 126 million users
In July 2018, Apollo left a database containing billions of data points publicly exposed. A subset of the data was sent to Have I Been Pwned which had 126 million unique email addresses. The full dataset included personally identifiable information (PII) like names, email addresses, place of employment, roles held and location.
28. Badoo Data Breach

Date: July 2013
Impact: 112 million users
In June 2013, a data breach allegedly originating from social website Badoo was found to be circulated. The breach contained 112 million unique email addresses and PII such as names, birthdates and passwords stored as MD5 hashes.
29. Capital One Data Breach

Date: July 2013
Impact: 106 million credit card numbers
In July 2013, Capital One identified a security breach of its customer records that exposed the personal information of its customers, including credit card data, social security numbers, and bank account numbers.
30. Evite Data Breach

Date: August 2013
Impact: 101 million users
In April 2019, Evite, a social planning and invitation site identified a data breach from 2013. The exposed data included 101 million unique email addresses, as well as phone numbers, names, physical addresses, dates of birth, genders and passwords stored in plain text.
31. Quora Data Breach

Date: December 2018
Impact: 100 million users
Quora, a popular site for Q&A suffered a data breach in 2018 exposed the personal data of up to 100 million users.
The types of leaked data included personal information such as names, email addresses, encrypted passwords, user accounts linked to Quora and public questions and answers posted by users. There was no evidence discovered that anonymously posted questions and answers were affected by the breach.
32. VK Data Breach

Date: January 2012
Impact: 93 million users
Russian social media site VK was hacked and exposed 93 million names, phone numbers, email addresses and plain text passwords.
33. MyHeritage Data Breach

Date: June 2018
Impact: 92 million users
MyHeritage, a genealogical service website was compromised, affecting more than 92 million user accounts. The breach occurred in October 2017, but wasn't disclosed until June 2018. A security researcher discovered a file on a private server containing email addresses and encrypted passwords. The security team at MyHeritage confirmed that the content of the file affected the 92 million users, but found no evidence that the data was ever used by the attackers. MyHeritage earned praise for promptly investigating and disclosing details of the breach to the public.
34. Youku Data Breach

Date: December 2016
Impact: 92 million users
Youku a Chinese video service exposed 92 million unique user accounts and MD5 password hashes.
35. Rambler Data Breach

Date: March 2014
Impact: 91 million users
A dump of 91 million accounts from Rambler ("Russian Yahoo") was traded online containing usernames (that form part of a Rambler email) and plain text passwords.
36. Facebook Data Breach (2018)

Date: early 2018 (this is when a Cambridge Analytica whistleblower disclosed the story)
Impact: 87 million users
Though a slightly different type of data breach as the information was not stolen from Facebook, the incident that affected 87 million Facebook accounts represented the use of personal information for purposes that the affected users did not appreciate. Cambridge Analytica was a data analytics company that was commissioned by political stakeholders including officials in the Trump election and pro-Brexit campaigns. Cambridge Analytica acquired data from Aleksandr Kogan, a data scientist at Cambridge University, who harvested it using an app called "This Is Your Digital Life". One of the most controversial elements of this breach was that users did not appreciate or consent to the political usage of data from a seemingly-innocuous lifestyle app.
UpGuard's researchers also discovered and disclosed a related breach by AggregateIQ, a Canadian company with close ties to Cambridge Analytica. Details about these discoveries can be found in our Aggregate IQ breach series (part 1, part 2, part 3 and part 4).
37. Dailymotion Data Breach

Date: October 2016
Impact: 85 million users
In October 2016, Dailymotion a video sharing platform exposed more than 85 million user accounts including emails, usernames and bcrypt hashes of passwords.
38. Anthem Data Breach

Date: February 2015
Impact: Theft of up to 78.8 million current and former customers
In February 2015, a single user at an Anthem subsidiary clicked on a phishing email which gave attackers access to:
- Names
- Addresses
- Dates of birth
- Employment histories
- Social security numbers
- Health identification numbers
The attack also affected other brands through the Anthem network, including Blue Cross, Blue Shield, Amerigroup, Caremore, and Unicare. The breach was undiscovered and undetected for weeks while the hackers stole information from Anthem servers. Although the data was not required to be encrypted, Anthem still faced backlash for failing to protect user data.
In 2017, Anthem paid a record $115 million as part of a landmark class-action settlement in one of the largest healthcare data breaches of all time. Additionally, Anthem also settled with the Department of Health and Human Services (HHS) for $16 million for failing to implement appropriate measures to detect hackers and unauthorized network activity.
39. Dropbox Data Breach

Date: mid-2012
Impact: 69 million users
In mid 2012, Dropbox suffered a data breach which exposed 68 million records that contained email addresses and salted hashes of passwords (half SHA1, half bcrypt).
40. tumblr Data Breach

Date: February 2013
Impact: 66 million users
In February 2013, tumblr suffered a data breach that exposed 65 million accounts. The breach included email addresses and salted SHA1 password hashes.
41. Uber Data Breach

Date: Late 2016
Impact: Personal information of 57 million Uber users and 600,000 drivers exposed.
In late 2016, Uber learned that two hackers were able to access the names, email addresses, and mobile phone numbers of 57 million users of the Uber app. They also got the driver's license numbers of 600,000 Uber drivers. In addition, the hackers were able to access Uber's GitHub account, where they found Uber's Amazon Web Services credentials.
42. The Home Depot Data Breach

Date: September 2014
Impact: Exposure of the credit card information of 56 million customers
Home Depot announced that its POS (point-of-sale) systems had been infected with a custom-built malware, which posed as antivirus software, affecting customers from across the US and Canada. After investigation, cyber law enforcement discovered that the cybercriminals most likely breached Home Depot's servers through a third-party supplier, which allowed them to steal payment information undetected for almost five months.
After the attack and damages resulting in over $180 million, Home Depot promised to invest in cybersecurity to better protect sensitive financial data. Most of the damages included payments to affected individuals, credit card companies, banks, and lawsuits.
43. TJX Companies Inc. Data Breach

Date: Jul 2005
Impact: 45.6 million card numbers
TJX, the owner of a number of retail brands, had one of its payment systems breached exposing over 45 million credit and debit card numbers. The data was garnished over several waves of breaches
The breaches occurred over several occasions ranging from July 2005 to January 2007.
TJX claimed that the names and addresses associated with each stolen card number were not exposed in the breach.
44. Target Data Breach

Date: November 2013
Impact: 32 million users.
Target was compromised through a third-party data breach. The attack vector was a portal used to share data with third-party vendors. This portal created a pathway into Target’s network, ultimately leading to the compromise. of over 41 million credit and debit card numbers.
Target was slapped with multiple fines, including a $19 million class-action lawsuit.
45. Ashley Madison Data Breach

Date: July 2015
Impact: 32 million users.
Hacking group identified as Impact Team compromised 35 million user records from the cheating website Ashley Madison.
The hackers demanded that parent company Avid Life Media shut down Ashley Madison and sister website Established Men within 30 days to avoid the publication of compromised records.
Avid Life Media failed to comply which resulted in wave after wave of categorised data dumps in Pastebin. The list of exposed users included members of the military and government.
The following records were included in the accessed data:
- Seven years worth of credit card payment history
- Full names
- Residential Addresses
- Email addresses
- Descriptions of what members were seeking
Impact Team claimed the breach was easy to achieve with little to no security to bypass.
Read the news article by Wired about this event >
46. LastPass Data Breach

Date: August 2022
Potential Impact: 30 million users.
In a well-planned advanced persistent attack, which involved bypassing complex security measures like MFA, hackers compromised the laptop of a LastPass DevOps engineer to gain access to customer personal vaults. The incident potentially impacted 30 million of LastPass’ users, calling into question the efficacy of the company’s information security measures.
Learn more about the LastPass Data breach >
47. Plex Data Breach

Date: August 2022
Impact: 20 million users
Streaming platform Plex suffered a data breach impacting most of its users, approximately 20 million. The following types of sensitive information were compromised in the cyberattack:
- Usernames
- Email Addresses
- Passwords
In an email to its users, Plex assured its users that all compromised passwords were hashed and secured in accordance with best cybersecurity practices.
48. Bonobos Data Breach

Date: January 2021
Impact: 12.3 million records
Men’s clothing store Bonobos suffered a data breach in 2021 after a cybercriminal compromised its backup server containing customer data.
The following categories of data were accessed, amounting to the 12.3 million total:
- 7 million shipping address records
- 1.8 million account information records
- 3.5 million partial credit card records.
This database was not connected to Bonobo’s private data, which was siloed for protection. But threat actors could still exploit the stolen information.
After the stolen data was dumped on a hacker forum, a threat actor claimed to have uncovered 158,000 hashed SHA-256 passwords. But the remaining passwords hashed with SHA-512 could not be cracked.
49. MGM Grand Data Breach

Date: Feb 2020
Impact: 10.6 million customers.
Hackers gained access to over 10 million guest records from MGM Grand. The records exposed the contact information of former hotel guests including Justin Bieber, Twitter CEO Jack Dorsey, and government officials.
MGM Grand assures that no financial or password data was exposed in the breach.
50. Optus Data Breach

Date: Sep 2022
Impact: 9.8 million customers.
Cybercriminals gained aceess to Optus' internal network, gaining access to a customer data base pertaining to up to 9.8 million customers. The compromised data, dates as far back as 2017, included the following types of information:
- Names
- Birth dates
- Phone numbers
- Email addresses
Sub sets of data also includes street addresses, drivers licenses, and passport numbers.
It’s speculated that the cybercriminal group gained access through an unauthorized API endpoint, meaning a user/password or any other authentication method wasn't required to connect to the API.

51. Medibank Data Breach

Date: November 2022
Impact: 9.7 million records.
Using stolen privileged credentials procured on the dark web, a cybercriminal gained access to Medibank’s internal systems. After locating the company’s sensitive customer data resources, the hackers deployed a script to automate the data theft process. When exfiltration was complete, 200 GB of customer data was stolen from Medibank, impacting 9.7 million customers.
Compromised records included:
- Names
- Birth dates
- Passport numbers
- Information on medicare claims
52. Easyjet Data Breach

Date: May 2020
Impact: 9 million customers.
A highly sophisticated cyber attack breached exposed the data of 9 million easyJet customers.
Data accessed in the breach included travel details email addresses as well as the complete credit card details of 2,208 customers.
Because customer credit card information was leaked, this cyber attack exposes Easyjet’s breach of the General Data Protection Regulation, which could result in a fine of up to 4% of its global annual turnover.
53. 123RF Data Breach

Date: Nov 2020
Impact: 8.3 million records
8.3 million database records from popular stock photo and vector image seller 123RF were copied and posted for sales on a hacker forum.
The compromised data included:
- Phone numbers
- Addresses
- Paypal email’s
- IP addresses
- MD5 hashed passwords.
ImagineGroup (the owner of 123RF) assured that no financial information was accessed in the breach and that all user passwords were encrypted.
However, data breach investigators BleepingComputer managed to successfully convert the hashed passwords of numerous accounts to plain-text using online MD5 cracking tools.
Though this breach did not directly expose financial information, if compromised users recycled their Paypal passwords when signing up to 123RF, they’re at a high risk of suffering financial theft.
54. Twitch Data Breach

Date: October 2021
Impact: 7 million users (potentially)
Twitch, an Amazon-owned company, suffered a breach of almost its entire code base. The exact impact of the incidents hasn’t been confirmed, but given its depth of compromise, it has the potential of impacting all of Twitch’s users.
125GB of sensitive data was posted via a torrent link on the anonymous forum 4chan.

The sensitive data leaks include:
- The entirety of Twitch’s source code.
- Three years of payout reports for creators (including high-profile creators.
- All of Twitch’s properties (including IGDB and CurseForge).
- Code related to proprietary SDKs and internal AWS services used by Twitch.
- The identity of an unreleased steam competitor from Amazon Game Studios - “Vapor”
- Twitch’s internal ‘red teaming tools’, used by internal security teams for cyberattack training exercises.
Though Twitch admitted in its statement that a subset of creator payout data was also accessed, the company assures that credit card number and bank information was not compromised.
The security vulnerability that made the breach possible was a server configuration change permitting unauthorized access by third parties. This has now been remediated.
Most cybercriminals post stolen data for sale after a breach, but the unidentified cybercriminal - who was likely using a proxy server - was not interested in monetary gain. Instead, their objective was to call a mass disruption to punch Twitch for fostering a toxic community of users.
55. Marriott Data Breach

Date: March 2020
Impact: 5.2 million guests
Marriott has once again fallen victim to yet another guest record breach. On March 31, the company announced that up to 5.2 million records were compromised. Some of the records accessed include
While the exact list of records breached is yet to be conformed, it’s believed that the following guest records were compromised:
- Email address
- Mail addresses
- Phone numbers
- Company names
- Gender
- Birth dates
- Accommodation preferences
- Language preferences
- Linked airline loyalty programs and numbers
Marriott stated in its press release that the breach is not believed to have exposed pin numbers, payment card information, national IDs, drivers license numbers or loyalty card passwords.
By multiplying its internal login authentications and continuously scanning for data breaches, Marriott could mitigate, or completely prevent future cyber attacks.
56. Neiman Marcus Data Breach

Date: September2021
Impact: 4.8 million customers
US-based retailer, Neiman Marcus, has confirmed in a statement that an “unauthorized party” can access to sensitive customer information including:
- Usernames.
- Passwords.
- Security questions
- Financial information.
The breach impacted almost 3.1 million payment and virtual gift cards, of which more than 85% were either expired or no longer valid.
After learning of the incident, Neiman Marcus Group contacted impacted customers that had not changed their password since May 2020, urging them to immediately do so.
The incident highlights the danger of using the same password across different registrations. If this cybersecurity best practice isn’t followed, a single compromise could result in a victim suffering multiple breaches.
57. MeetMindful Data Breach

Date: January 2021
Impact: 2.28 million users.
MeetiMindful, a dating app focusing on the mindful community, was breached by a well-known hacker by the name of ShinyHunters.

Breached MeetMindful data dumped on dark web hacker forum - Source: ZDNet
Personal messaged between users was not compromised, but the following private information was exposed:
- IP addresses
- Real names
- Email addresses
- City, state, and ZIP details
- Facebook user IDs
- Facebook authentication tokens
- Dating preferences
- Marital status
- Birth dates
- Bcrypt-hashed account passwords
58. Pixlr Data Breach

Date: January 2021
Impact: 1.9 million users
A database of 1.9 million user records belonging to online photo-editor Pixlr was dumped on a dark web hacker forum by notorious cybercriminal ShinyHunters.

Exposed data included:
- Usernames
- Email addresses
- Country
- Hashed passwords
The data was stolen when the 123RF data breach occurred.
59. Tackle Warehouse LLC, Running Warehouse LLC, Tennis Warehouse LLC, and SkateWarehouse LLC Data Breaches

Date: October 2021 (disclosed December 2021)
Impact: 1.8 million people
Four online sports stores fell victim to a cyberattack resulting in the theft of highly-sensitive customer information including credit card data.
The data breach was disclosed in December 2021 by a law firm representing each sports store. The data breach was discovered by the impacted websites on October 15.
The following websites were impacted:
- Tackle Warehouse LLC (tacklewarehouse.com)
- Running Warehouse LLC (runningwarehouse.com)
- Tennis Warehouse LCC (tennis-warehouse.com)
- Skate Warehouse LLC (skatewarehouse.com)
The specific security vulnerabilities and attack methods that facilitated the breach have not been disclosed, but it’s speculated that access was achieved via a database breach.
The following data was compromised in the cyberattack:
- Customer names
- Credit card numbers (with CVV)
- Debit card numbers (with CVV)
- Website account passwords
At the time of writing this, it is unknown whether the compromised credit card numbers were complete or hashed. Even if hashed, they could still be unencrypted with sophisticated brute force methods.
Whoever is at fault for this breach will likely suffer tough financial regulatory consequences for their security negligence.
60. Harbour Plaza Hotel Management Data Breach

Date: February 2022
Impact: 1.2 million records
Harbour Plaza Hotel Management, a hospitality management company in Hong Kong, suffered a breach of its accommodation reservation databases, impacting approximately 1.2 million customers.
According to the FAQs related to the incident, Harbour Plaza is yet to confirm whether cybercriminals managed to decrypt encrypted credit card data included in the breach.
61. Graff Data Breach

Date: November 2021
Impact: 1.1 million records
Exclusive UK Jeweller, Gaff, suffered a data breach that compromised many of its famous clients. The Russian cybercriminal group, Conti, was responsible for the attack which involved the deployment of ransomware (ransom software).
After stealing Gaff's sensitive data and encrypting their internal systems, Conti started publishing some of the stolen records on the dark web, promising to only stop of their ransom of up to ten millions of pounds is paid.
To prove they weren't bluffing, Conti published 11,000 records on the dark web, which according to the Russian cybercriminals, represents just 1% of the total records that were stolen.
The stolen records include client names, addresses, invoices, receipts and credit notes.
Some of the high-profile customers reportedly impacted by this breach include:
- Donald Trump
- David Beckham
- Oprah Winfrey
- Alec Baldwin
- Sir Philip Green
- Ghislaine Maxwell
- Saudi Crown Prince Mohammed bin Salman
- Sheikh Mohammed bin Rashid Al Maktoum
62. Los Angeles Unified School District (LAUSD)

Date: September 2022
Impact: 1000 schools / 600,000 students / 500GB of data
In one of the biggest data breaches of all time in the education industry, the Los Angeles Unified School District (LAUSD) was attacked by Vice Society, a Russian criminal hacking group. The attack affected over 1000 schools and 600,000 students in the second-largest school district in the United States. The ransomware attack occurred over Labor Day weekend, and prevented LAUSD officials from accessing important data, including:
- Personal information (names, physical addresses, phone numbers)
- Email addresses
- Computer systems and applications
- Passport details
- Employee social security numbers
- Employee account login information
- Tax forms
- Contracts and legal documents
- Financial reports
- Banking details
- Health information (including COVID-19 vaccination data)
- Background checks and conviction reports
- Student psychological assessments
- VPN credentials
After consulting with CISA and the FBI, LAUSD released a statement saying they would not be paying the ransom that Vice Society had demanded. As a result, Vice Society released the stolen data on their dark web forum. Although the lasting impact of the attack has yet to be determined, there could be potential litigations in the coming years due to negligence and mishandling of sensitive data. Prior to the attack, LAUSD was told of potential vulnerabilities in their systems but the school district failed to act to remediate the issues.
63. Zoom Data Breach

Date: April 2020
Impact: 500,000 users.
When Zoom sign ups were nearing their pandemic peak in April of 2020, hackers breached 500,000 accounts and either sold or freely published them on the dark web.
Hackers initially canvassed dark web databases of previously compromised login credentials dating back to 2013. Because passwords are usually recycled, this gave them instant access to a swathe of active Zoom accounts.
A series of credential stuffing attacks was then launched to compromise the remaining accounts.
Recipients of compromised Zoom accounts were able to log into live streaming meetings.
64. Slickwraps Data Breach

Date: Feb 2020
Impact: 370,000 customers
Slickwraps, a manufacturer of vinyl skins for phones and tablets, suffered a breach impacting 370,000 of its customers.
This breach could have been avoided if Slickwraps listened to the warnings of a white hat hacker highlighting the company’s terrible cybersecurity. After being ignored, the hacker echoed his concerts in a medium post.
Slickwraps still ignored the warnings.
Before the medium post was deleted, a second hacker read it and decided to also try to convince Slickwraps but with a slightly more impactful approach.
The second hacker actually breached Slickwraps’s abysmal defences and announced their cybersecurity complacency in an email to over 370,000 of its customers.
Let's hope SlickWraps finally strengthens their cybersecurity framework after such a tumultuous history.

65. Magellan Health Data Breach

Date: Apr 2020
Impact: 365,000 patients
Magellan Health, a Fortune 500 company has been the victim of a sophisticated ransomware attack where over 365,000 patient records were breached.
Employee login information was first accessed from malware that was installed internally. Then, by posing as a Magellan client in a phishing attack, the hackers gained access to a single corporate server and implemented their ransomware.
Included in the breached data was patient social security numbers, W-2 information and employee ID numbers.
66. Nintendo Data Breach

Date: April 2020
Impact: 300,000 accounts.
300,000 Nintendo accounts were compromised and used to make unsolicited digital purchases. The number affected accounts was almost doubled from the originally stated 140,000 upon further investigation.
The following information was exposed:
- Account passwords
- Account owner name
- DOB
- Email addresses
- Country of residence
While it isn’t clear how hackers gained access to accounts, it’s speculated that weak passwords are to blame. To prevent further breaches, Nintendo posted a tweet asking members to enable 2-step authentication.
67. Mailfire Data Breach

Date: September 2020
Impact: 100,000 users
Mailfire, an email marketing software used by adult dating sites and ecommerce websites, had its database breached exposing personal user records from over 70 websites.
The breach occurred through Mailfire’s unsecured Elasticsearch server. Onced breached, the hacker had access to over 320 million records from notifications being pushed out to Mailfire clients.
The records exposed included private conversations between adult dating site members as well as the following Personally Identifiable Information:
- Name
- Age
- DOB
- Gender
- Location of message senders
- IP addresses
- Member profile pictures
- Member bio descriptions
Besides the personal information of website members, this data breach also exposed many scam dating websites with fabricated female profiles..
68. Antheus Tecnologia Data Breach

Date: March 2020
Impact: 76,000 fingerprints
Antheus Tecnologia, a Brazilian biometrics company specializing in the development of fingerprint identification systems, suffered a breach to its server which could potentially expose 76,000 unique fingerprint records.
The data accessed consists of 2.3 millions data points which could be reverse engineered to recreate each original fingerprint.
Besides finger print data points, 81.5 million records were accessed, consisting of email addresses, employee telephone numbers and administrator login information.
69. SolarWinds Data Breach

Date: March 2020
Impact: 18,000 businesses
In March 2020, nation-state hackers believed to be from Russian, compromised a DLL file linked to software update for the Orion platform by SolarWinds. The supply chain attack impacted up to 18,000 SolarWinds customers including six U.S Government departments. The attack wasn’t discovered until December 2020.
This incident was the impetus to Joe Biden's Cybersecurity Executive Order that now enforces all organizations to strengthen their supply chain security efforts
The highly sophisticated hackers are believed to also be responsible for the FireEye cyberattack resulting in the theft of its Red Team Assessment tools - a set of tools developed by FireEye to discover cyberattack vulnerabilities within any organizations.
Given that FireEye’s clientbase includes government entities, it is further speculated that these Red Team Assessment tools made the U.S. Government data breach possible - an attack labeled by cyber security experts as the biggest breach in the nation’s security history.
The list of victims continues to grow. To check if you've been impacted, you should perform a thorough risk assessment for each vendor.
70. Pegasus Airline Data Breach

Date: March 2022
Impact: 6.5 Terabytes of data
A misconfigured AWS bucket led to the compromise of 23 million files belonging to the Turkish airline company Pegasus Airlines. The security exposure was discovered by the security company Safety Detectives.
The data was linked to the airline’s EFB software, a solution requiring access to take off, landing, and refueling data and sensitive flight crew information.
The AWS bucket misconfiguration meant that anyone had free access to this database, including nearly 400 files with plain text passwords and secret keys.
When the exposure was reported, Pegasus Airlines didn’t find evidence of data compromise. However, while the AWS bucket remained misconfigured, cybercriminals may have clandestinely exfiltrated the exposed data.
71. Philippines COMELEC Data Breach

Date: January 2022
Impact: 60 GB of data
A hacker group breached the security systems of the Commission on Elections (COMELEC) for the Republic of the Philippines, compromising 60 gigabytes of sensitive voter information.
The depth of this information could allow the cybercriminals to potentially map the complete internal operations of the election system in the Philippines, paving the road to more devastating follow-up attacks at a national security level.
The compromised data included usernames and PINS for vote-counting machines (VCM).
72. MailChimp Data Breach

Date: Apr 2022
Impact: 100 clients
How did the data breach occur?
Mailchimp fell victim to a data breach after cybercriminals gained access to a tool used by internal customer support and account administration teams following a successful social engineering attack. However, this initial breach was just the preliminary stage of the entire cyber attack plan.
While desperately scouring the client email lists stored in Mailchimp’s internal tools, the cybercriminals finally found what they were looking for - an email list of customers of the hardware cryptocurrency wallet, Trezor.
The cybercriminals then sent a very convincing phishing email to this entire customer list claiming that a critical security incident occurred, requiring an urgent download of a patched version of the Trezor app.

When clicked, this link directed users to a malicious website almost indistinguishable from Trezor’s website. To access the fraudulent app, users needed to submit their recovery seed - a list of ordered words used to recover access to a crypto wallet.
What data was compromised?
Investigations are still underway, so the complete impact of this phishing attack isn’t yet known. In the phishing email, the cybercriminals claimed that 106,852 accounts were compromised. This number may represent the total number of email accounts targeted in the phishing campaigns, but that hasn’t yet been confirmed.
What is confirmed, at this point, is that approximately 100 Mailchimp client accounts were compromised in the initial phase of the cyberattack.
Follow Trezor’s blog to track the progress of investigation efforts.
This cyber incident highlights the frightening sophistication some phishing attackers are capable of.
























![Largest Data Breaches in US History [Updated for 2023]](https://nulld3v.com/uploads/images/202311/image_430x256_654e69df8d469.jpg)










