Second Data Leak Hits Chess.com; 476,000 User Records Exposed
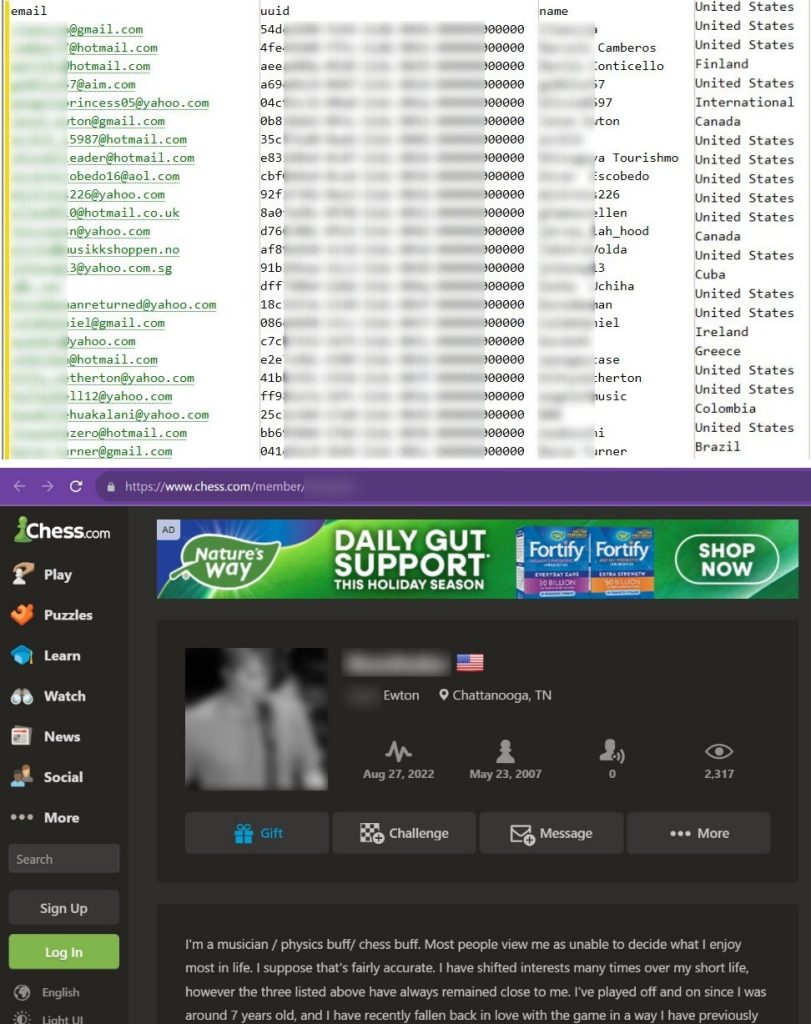
The data leak, which includes sensitive information like full names, email addresses, usernames, and profile links, puts Chess.com users at substantial risk of identity theft and phishing attacks.

Hackread.com recently revealed that cybercriminals exploited Chess.com's "find friends" feature in its API to gather publicly available user data. On November 10th, 2023, the site reported the disclosure of a database scraped from Chess.com, containing details of approximately 828,327 users, which was leaked on the infamous Breach Forums.
Following this, over the weekend, another dataset from Chess.com was leaked by a different cybercriminal. This latest database impacted nearly half a million (476,121) users of the popular online chess platform and social networking site. Remarkably, this same forum had also hosted a leaked scraped database from LinkedIn just days earlier, affecting 25 million users.
Like the earlier breach, the most recent incident resulted in the exposure of private user information. The leaked data encompasses full names, usernames, profile URLs, email addresses, the countries of users, avatar URLs (profile images), Universal Unique Identifiers (UUID), user IDs, and the dates of registration.
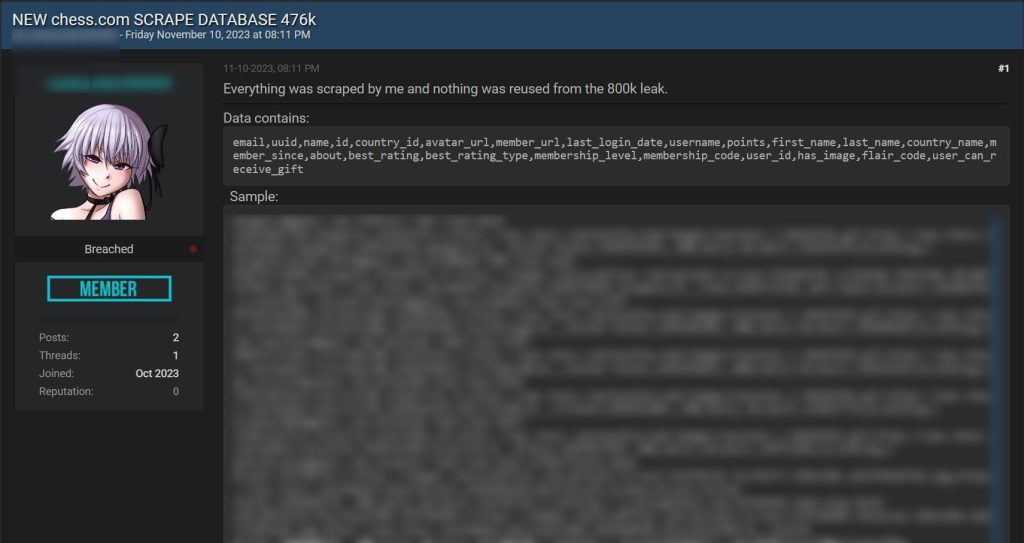
In a post on Breach Forums, the threat actor specified that the recently published data leak is distinct and unrelated to the previous one involving the 800,000 scraped records.
According to the threat actor, no data from the earlier leak has been incorporated into the current leak. “Everything was scraped by me and nothing was reused from the 800k leak,” the actor wrote.
A quick analysis by Hackread.com can confirm the actor’s claims to be authentic and no data was taken from the previous leak.
Importantly, Chess.com itself has not been hacked, and its servers remain secure. The issue stems from threat actors exploiting Chess.com's public API. Chess.com acknowledged this, stating, "This was NOT a data breach. Our infrastructure, member accounts, and data such as passwords are secure." They explained that the "find friends" feature of their API was used to match email addresses with Chess.com accounts, and this publicly available information was published.
Despite the data being publicly accessible, the inclusion of email addresses in the leaked information poses risks to users. The data could be used for malicious purposes like identity theft or phishing attacks, where cybercriminals could impersonate Chess.com in fraudulent emails.
Web scraping, the process used by these data scrapers, is a technique for extracting information from websites. It is a challenging activity to block, especially for large websites like Chess.com. While preventive measures like rate limiting and captcha challenges are in place, scrapers often find ways to circumvent these safeguards. Not all scraping is malicious; it is also used for legitimate purposes such as research and machine learning. However, in cases like this, it raises concerns about user privacy and security.
























![Largest Data Breaches in US History [Updated for 2023]](https://nulld3v.com/uploads/images/202311/image_430x256_654e69df8d469.jpg)









![[code] Microsoft Windows 11 - 'apds.dll' DLL hijacking (Forced)](https://nulld3v.com/uploads/images/202311/image_430x256_654d296d9fa02.jpg)


