Boeing data amounting to gigabytes is leaked by LockBit ransomware.
The LockBit ransomware group has released data they pilfered from Boeing, a leading aerospace company that provides services for commercial aircraft and defense systems. [...]

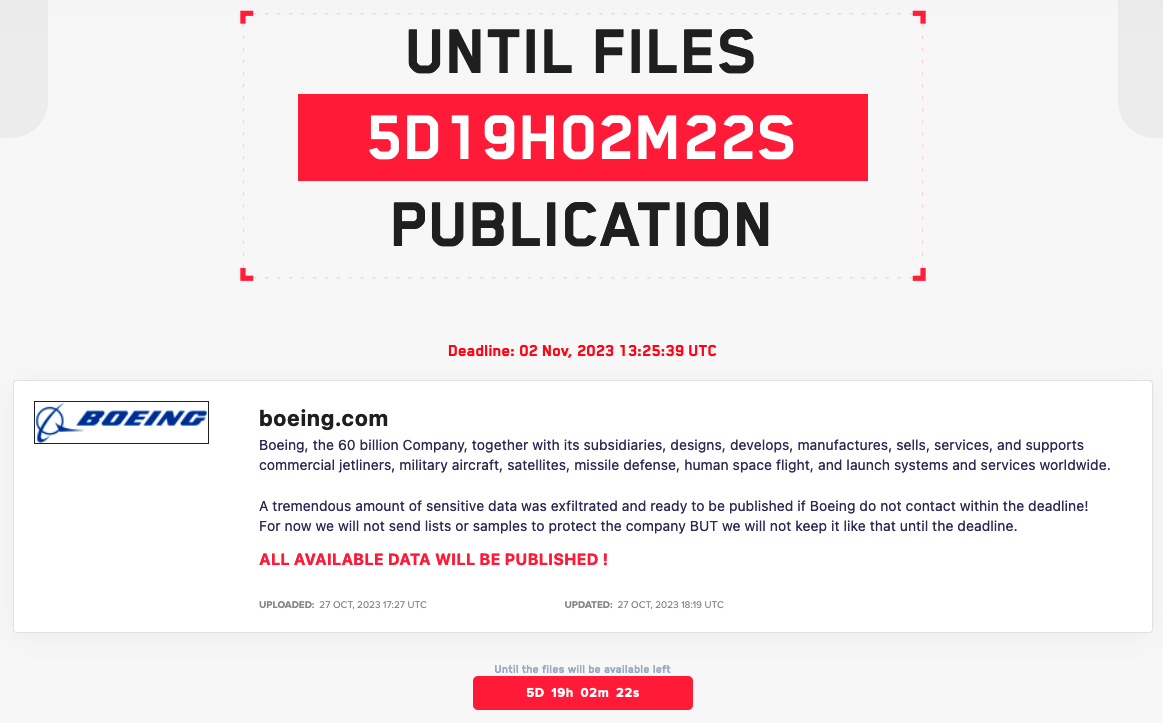
The LockBit ransomware group has released over 43GB of Boeing's data, following the aerospace giant's refusal to meet their ransom demands. Prior to this leak, LockBit had cautioned Boeing that their data would be made public if their warnings were ignored. The group threatened to release approximately 4GB of Boeing's most recent files as a sample.
The data disclosed predominantly consists of backups for various systems, with the latest backup dated October 22. Boeing was listed on LockBit's leak site on October 27, and the company was given until November 2nd to initiate negotiations with the hackers.
LockBit claimed they had exfiltrated "a tremendous amount" of Boeing's sensitive data and expressed their readiness to publish it. This incident highlights the ongoing cybersecurity threats faced by major corporations, particularly in sensitive industries such as aerospace and defense.
source: BleepingComputer
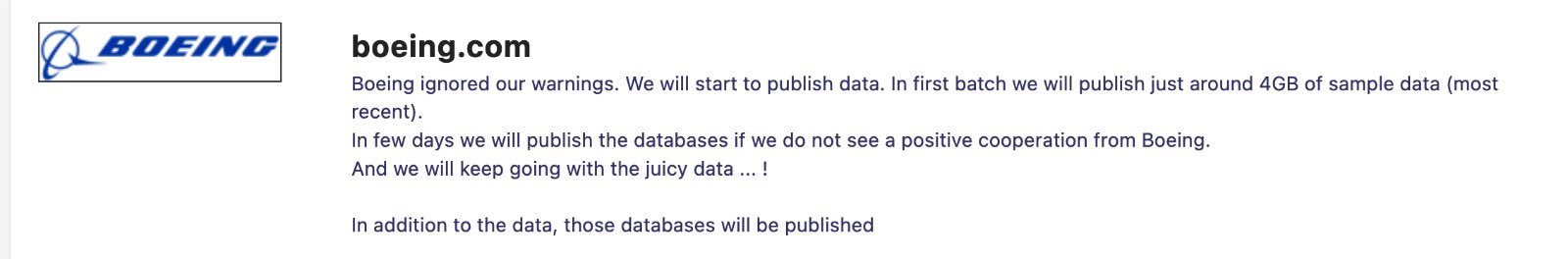
Boeing was temporarily removed from LockBit ransomware's list of victims but reappeared on November 7. The reappearance followed the company's lack of response to the hackers' warnings. In response to Boeing's silence, LockBit threatened to release a sample of the stolen data, approximately 4GB, claiming it to be the most recent files.
The ransomware group further warned that if Boeing continued to show no intent for cooperation, they would proceed to publish the company's databases. This move by LockBit underscored their readiness to leverage the stolen data as a means of pressuring Boeing into negotiation or compliance.
On November 10th, LockBit ransomware group released a cache of data they obtained from Boeing on their website. This batch of data included IT management software configuration backups and logs from monitoring and auditing tools, as well as backups from Citrix appliances. The inclusion of Citrix appliance data raised suspicions that the LockBit group might have exploited the recently exposed Citrix Bleed vulnerability (CVE-2023-4966), especially since a proof-of-concept exploit for this vulnerability became publicly available on October 24th.
Boeing acknowledged the cyberattack but has not disclosed specifics about the breach or how the attackers penetrated its network defenses.
LockBit, known for its ransomware-as-a-service (RaaS) operations, has been active for over four years. It has victimized thousands of entities across different industries, including major organizations like Continental, the UK Royal Mail, Italy's Internal Revenue Service, and the City of Oakland.
According to a statement from the U.S. government in June, LockBit has extorted approximately $91 million through nearly 1,700 attacks on various U.S. organizations since 2020. However, LockBit's operations are not confined to the United States. In August, the Spanish National Police alerted the public about a phishing campaign aimed at architecture firms in Spain, designed to infiltrate systems with LockBit's ransomware.
























![Largest Data Breaches in US History [Updated for 2023]](https://nulld3v.com/uploads/images/202311/image_430x256_654e69df8d469.jpg)








![[code] WordPress Plugin AN_Gradebook <= 5.0.1 - Subscriber+ SQLi](https://nulld3v.com/uploads/images/202311/image_430x256_654d29af21505.jpg)


